Here's a preview from my zine, How DNS Works! If you want to see more comics like this, sign up for my saturday comics newsletter or browse more comics!
 get the zine!
get the zine!
read the transcript!
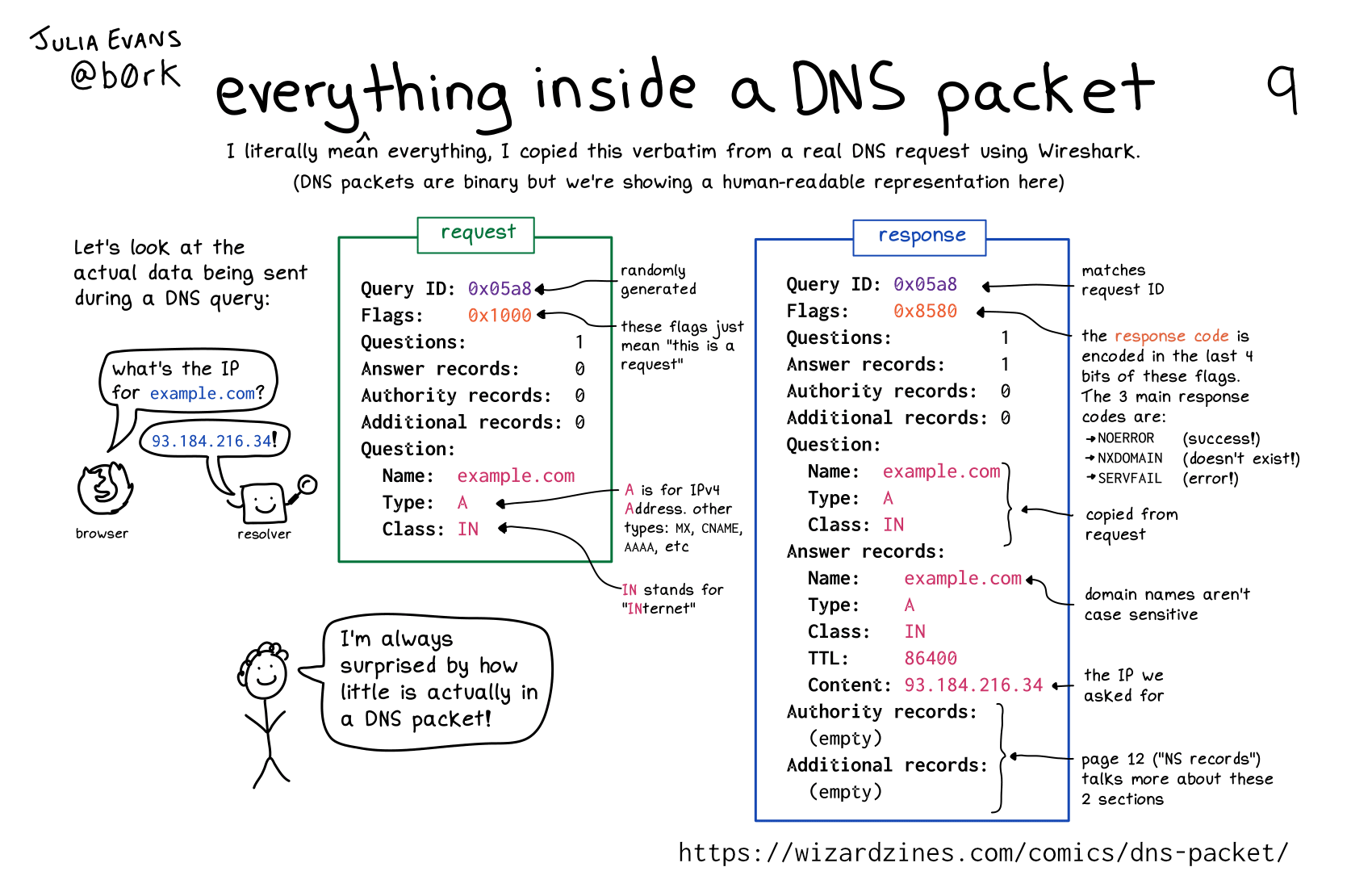
I literally mean everything, I copied this verbatim from a real DNS request using Wireshark. (DNS packets are binary but we’re showing a human-readable representation here)
Let’s look at the actual data being sent during a DNS query:
Illustration of a browser, represented by the Firefox logo of a fox wrapped around a globe, talking to a resolver, represented by a box with a smiley face holding a magnifying glass.
browser: what’s the IP for example.com?
resolver: 93.184.216.34!
request
Query ID: 0x05a8
(randomly generated)
Flags: 0x1000
(these flags just mean “this is a request”)
Questions: 1
Answer records: 0
Authority records: 0
Additional records: 0
Question:
Name: example.com
Type: A (A is for IPv4 address. other types: MX, CNAME, AAAA, etc) Class: IN`
(IN stands for “INternet”)
response
Query ID: 0x05a8
(matches request ID)
Flags: 0x8580
the response code is encoded in the last 4 bits of these flags. The 3 main response codes are:
- NOERROR (success!)
- NXDOMAIN (doesn’t exist!)
- SERVFAIL (error!)
Questions: 1
Answer records: 1
Authority records: 0
Additional records: 0
(copied from request)
Question:
Name: example.com
(domain names aren’t case sensitive)
Type: A
Class: IN
Answer records:
Name: example.com
Type: A
Class: IN
TTL: 86400
Content: 93.184.216.34
(the IP we asked for)
Authority records:
(empty)
Additional records:
(empty)
page 12 (“NS records”) talks more about these 2 sections
Illustration of a smiling stick figure with curly hair.
Person: I’m always surprised by how little is actually in a DNS packet!