Here's a preview from my zine, Bite Size Networking!! If you want to see more comics like this, sign up for my saturday comics newsletter or browse more comics!
 browse more comics!
get the zine!
browse more comics!
get the zine!
read the transcript!
panel 1:
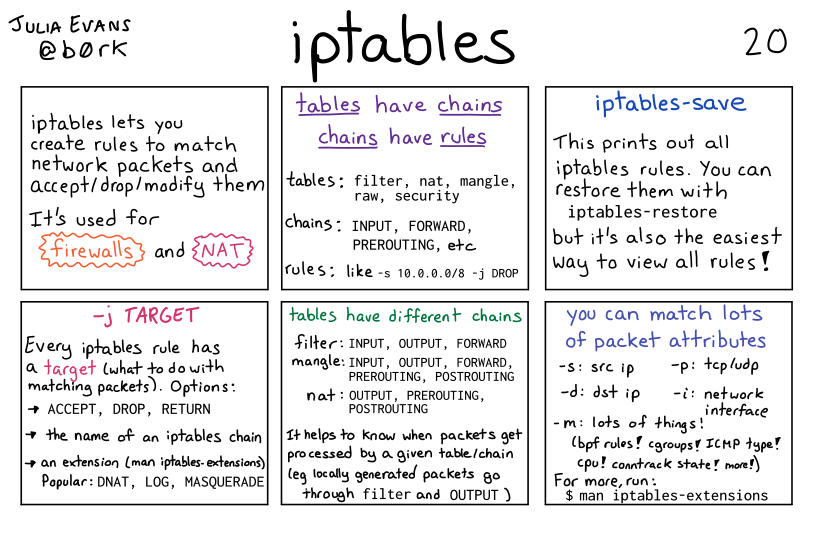
iptables lets you create rules to match network packets and accept/drop/modify them
It’s used for firewalls and NAT
tables have chains. chains have rules.
tables:
filternatmanglerawsecurity
chains:
INPUTFORWARDPREROUTING- etc
rules: like -s 10.0.0.0/8 -j DROP
iptables-save
This prints out all iptables rules. You can restore them with iptables-restore but it’s also the easiest way to view all rules.
-j TARGET
Every iptables rule has a target (what to do with matching packets). Options:
ACCEPT, DROP, RETURN- the name of an iptables chain
- an extension (man iptables.extensions)
Popular:
DNAT, LOG, MASQUERADE
tables have different chains
filter: INPUT, OUTPUT, FORWARD
mangle: INPUT, OUTPUT, FORWARD, PREROUTING, POSTROUTING
nat: OUTPUT, PREROUTING, POSTROUTING
It helps to know when packets get processed by a given table/chain (eg locally generated packets go through FILTER and OUTPUT
you can match lots of packet attributes
-s: src ip-d: tcp/udp-p: dst ip-i: network interface-m: lots of things! (bpf rules! gcroups! ICMP type! cp! conntrack state! more!
For more, run $ man iptables-extensions
Saturday Morning Comics!
Want another comic like this in your email every Saturday? Sign up here!