Here's a preview from my zine, How DNS Works! If you want to see more comics like this, sign up for my saturday comics newsletter or browse more comics!
 get the zine!
get the zine!
read the transcript!
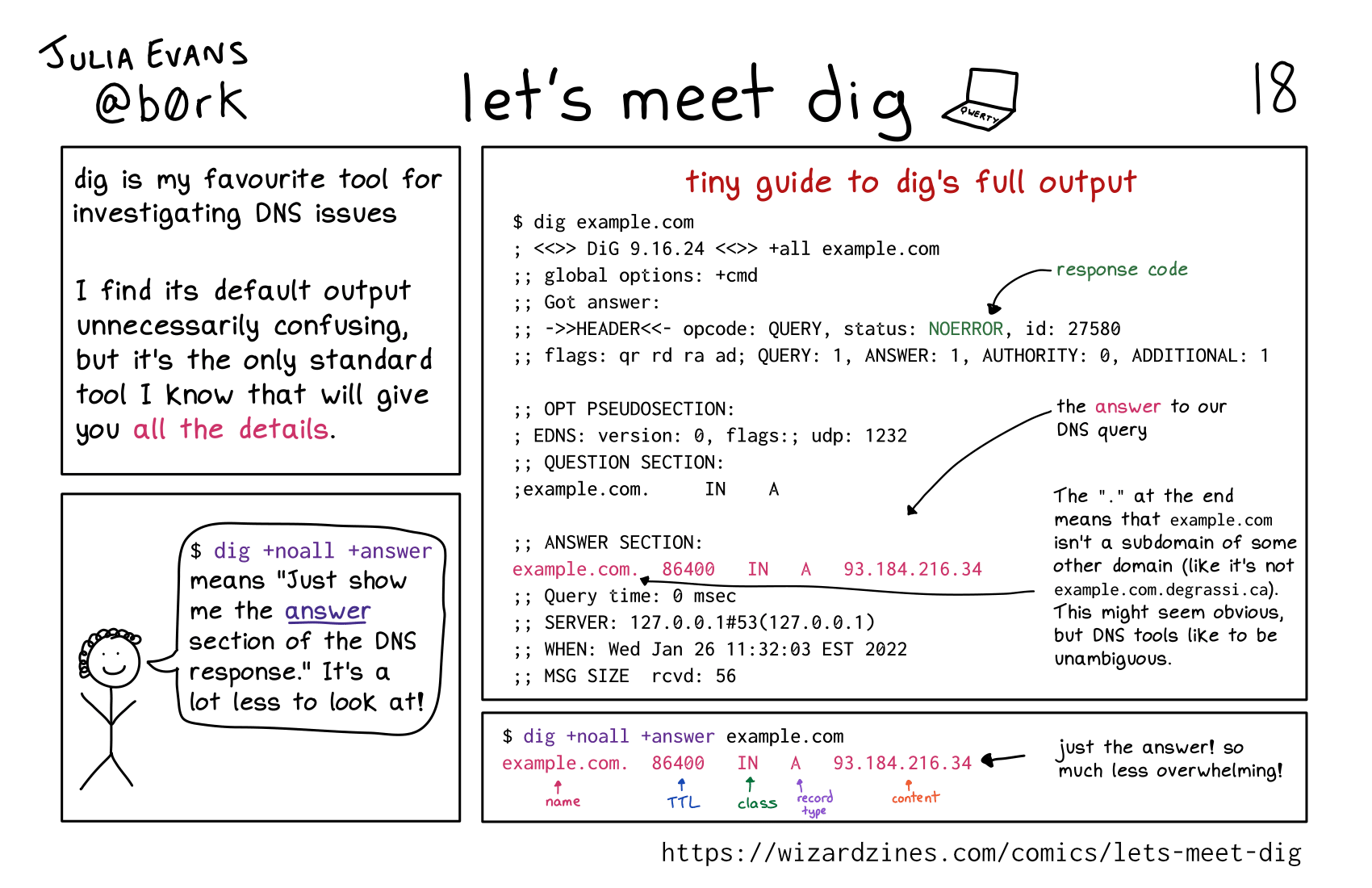
dig is my favourite tool for investigating DNS issues
I find its default output unnecessarily confusing, but it’s the only standard tool I know that will give you all the details.
tiny guide to dig’s full output
$ dig example.com
; <<>> DiG 9.16.24 <<>> +all example.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 27580
18
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
; example.com. IN A
;; ANSWER SECTION:
example.com. 86400 IN A 93.184.216.34
;; Query time: 0 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Wed Jan 26 11:32:03 EST 2022
;; MSG SIZE rcvd: 56
NOERROR is the response code
example.com. 86400 IN A 93.184.216.34 is the answer to our DNS query. The “.” at the end means that example.com isn’t a subdomain of some other domain (like it’s not example.com.degrassi.ca). This might seem obvious, but DNS tools like to be unambiguous.
panel 3:
Illustration of a smiling stick figure with curly hair.
person: $ dig +noall +answer means “Just show me the answer section of the DNS response.” It’s a lot less to look at!
panel 4:
$ dig +noall +answer example.com
example.com. 86400 IN A 93.184.216.34
example.com is the name
86400 is the TTL
IN is the class
A is the record type
93.184.216.34 is the content
just the answer! so much less overwhelming!