Here's a preview from my zine, How Containers Work! If you want to see more comics like this, sign up for my saturday comics newsletter or browse more comics!
 get the zine!
get the zine!
read the transcript!
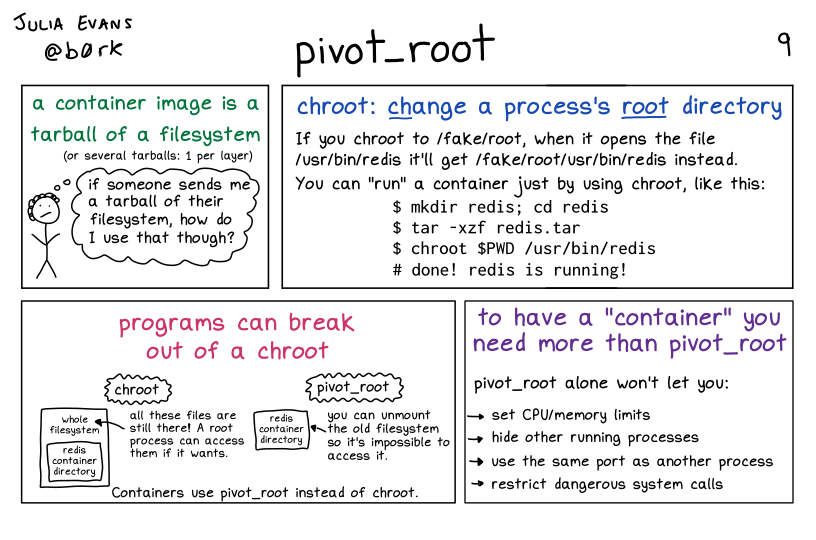
a container image is a tarball of a filesystem
(or several tarballs: 1 per layer)
pensive stick figure with short curly hair: if someone sends me a tarball of their filesystem, how do I use that though?
chroot: change a process’s root directory
If you chroot to /fake/root when it opens the file /usr/bin/redis it’ll get /fake/root/usr/bin/redis instead.
You can “run” a container just by using chroot, like this:
$ mkdir redis; cd redis
$ tar -xzf redis. tar
$ chroot $PWD /usr/bin/redis
# done ! redis is running!
programs can break out of a chroot
chroot:
Illustration of a box labelled “whole filesystem”. Inside it is another box labelled “redis container directory”.
All these files are still there! A root process can access them if it wants.
pivot_root
Illustration of a box labelled “redis container directory”.
You can unmount the old filesystem so it’s impossible to access it.
Containers use pivot_root instead of chroot.
to have a “container” you need more than pivot_root
pivot_root alone won’t let you:
- set CPU/memory limits
- hide other running processes
- use the same port as another process
- restrict dangerous system calls