Here's a preview from my zine, How Containers Work! If you want to see more comics like this, sign up for my saturday comics newsletter or browse more comics!
 get the zine!
get the zine!
read the transcript!
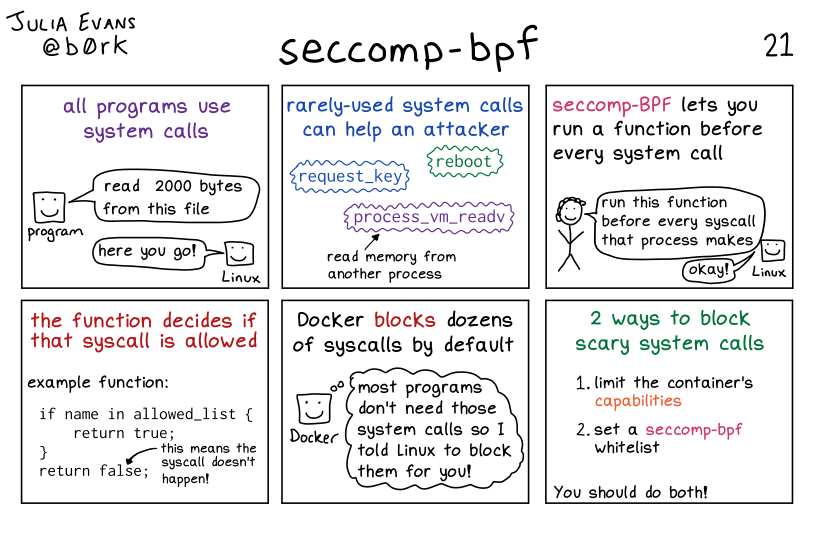
all programs use system calls
program, represented by a box with a smiley face: read 2000 bytes from this file
Linux, represented by a box with a smiley face:here you go!
rarely-used system calls can help an attacker
rebootrequest_keyprocess_vm_ready(read memory from another process)
seccomp-BPF lets you run a function before every system call
smiling stick figure with short curly hair: run this function before every syscall that process makes
Linux, represented by a box with a smiley face: okay!
the function decides if that syscall is allowed
example function:
if name in allowed_list {
return true;
}
return false;
return false means the syscall doesn’t happen!
Docker blocks dozens of syscalls by default
Docker, represented by a box with a smiley face: most programs don’t need those system calls so I told Linux to block them for you!
2 ways to block scary system calls
- limit the container’s capabilities
- set a seccomp-bpf whitelist
You should do both!