Here's a preview from my zine, Bite Size Networking! If you want to see more comics like this, sign up for my saturday comics newsletter or browse more comics!
 get the zine!
get the zine!
read the transcript!
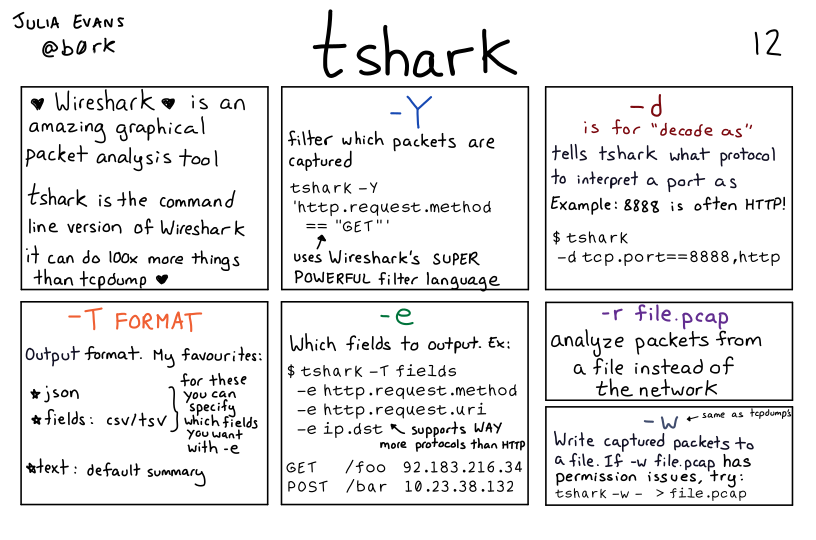
Wireshark is an amazing graphical packet analysis tool
(“Wireshark” has hearts around it)
tshark is the command line version of Wireshark
it can do 100x more things than tcpdump (heart)
-Y
filter which packets are captured
tshark -y
'http.request.method
== "GET"
(uses Wireshark’s SUPER POWERFUL filter language)
-d
is for “decode as”
tells tshark what protocol to interpret a port as
Example: 8888 is often HTTP!
$tshark
-d tcp.port==8888,http
-T FORMAT
Output format. My favourites:
- json
- fields: csv/tsv
(for these above two you can specify which fields you want with
-e) - text: default summary
-e
Which fields to output. Ex:
$tshark -T fields
-e http.request.method
-e http.request.uri
-e ip.dst
(supports WAY more protocols than HTTP)
GET /foo 92.183.216.34
POST /bar 10.23.38.132
-r file.pcap
analyze packets from a file instead of the network
-w
(same as tcpdump)
Write captured packets to a file. If -w file.pcap has permission issues, try tshark -w - > file.pcap