Here's a preview from my zine, How Containers Work! If you want to see more comics like this, sign up for my saturday comics newsletter or browse more comics!
 get the zine!
get the zine!
read the transcript!
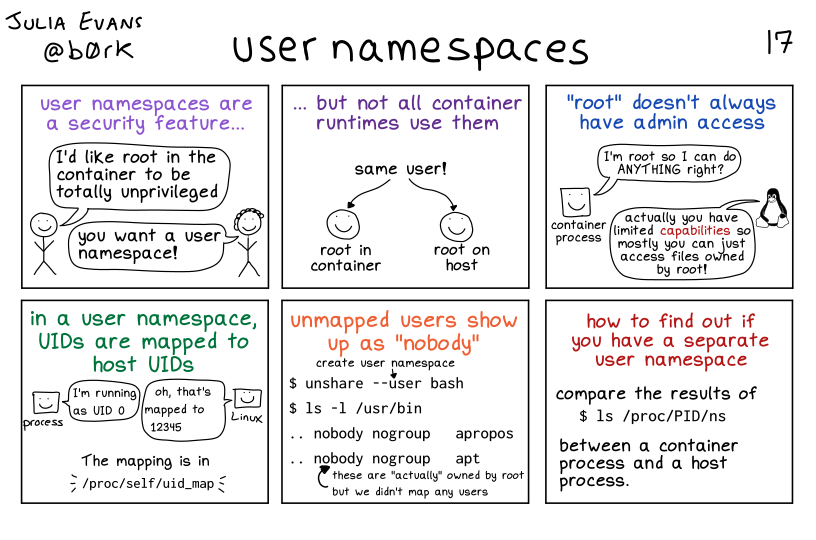
user namespaces are a security feature…
smiling bald stick figure: I’d like root in the container to be totally unprivileged
smiling stick figure with curly hair: you want a user namespace!
but not all container runtimes use them
same user!
(two arrows point to two smiley faces, one labelled “root in container”, the other labelled “root on host”)
“root” doesn’t always have admin access
Container process, represented by a box with a smiley face: I’m root so I can do ANYTHING right?
Tux: actually you have limited capabilities so mostly you can just access files owned by root!
in a user namespace, UIDs are mapped to host UIDs
process: I’m running as UID O
Linux: Oh, that’s mapped to 12345
The mapping is in /proc/self/uid_map
unmapped users show up as “nobody”
$ unshare --user bash (create user namespace)
$ ls -l /usr/bin
.. nobody nogroup apropos
nobody nogroup apt
(these are “actually” owned by root but we didn’t map any user)
how to find out if you have a separate user namespace
compare the results of
$ ls /proc/PID/ns
between a container process and a host process.